As cybercriminals continue to refine their social engineering tactics, a new practical resource from Blueclone Networks is giving New Jersey organizations a much-needed blueprint for defending one of their most vulnerable business systems: email.
The company has introduced a comprehensive Email Security Best Practices Guide designed specifically to help organizations reduce exposure to Business Email Compromise (BEC), account takeovers, phishing attacks, and invoice-fraud schemes that increasingly target small and mid-sized companies across the state. The guide focuses on real-world protections that can be deployed immediately, without requiring large security teams or enterprise-level budgets.
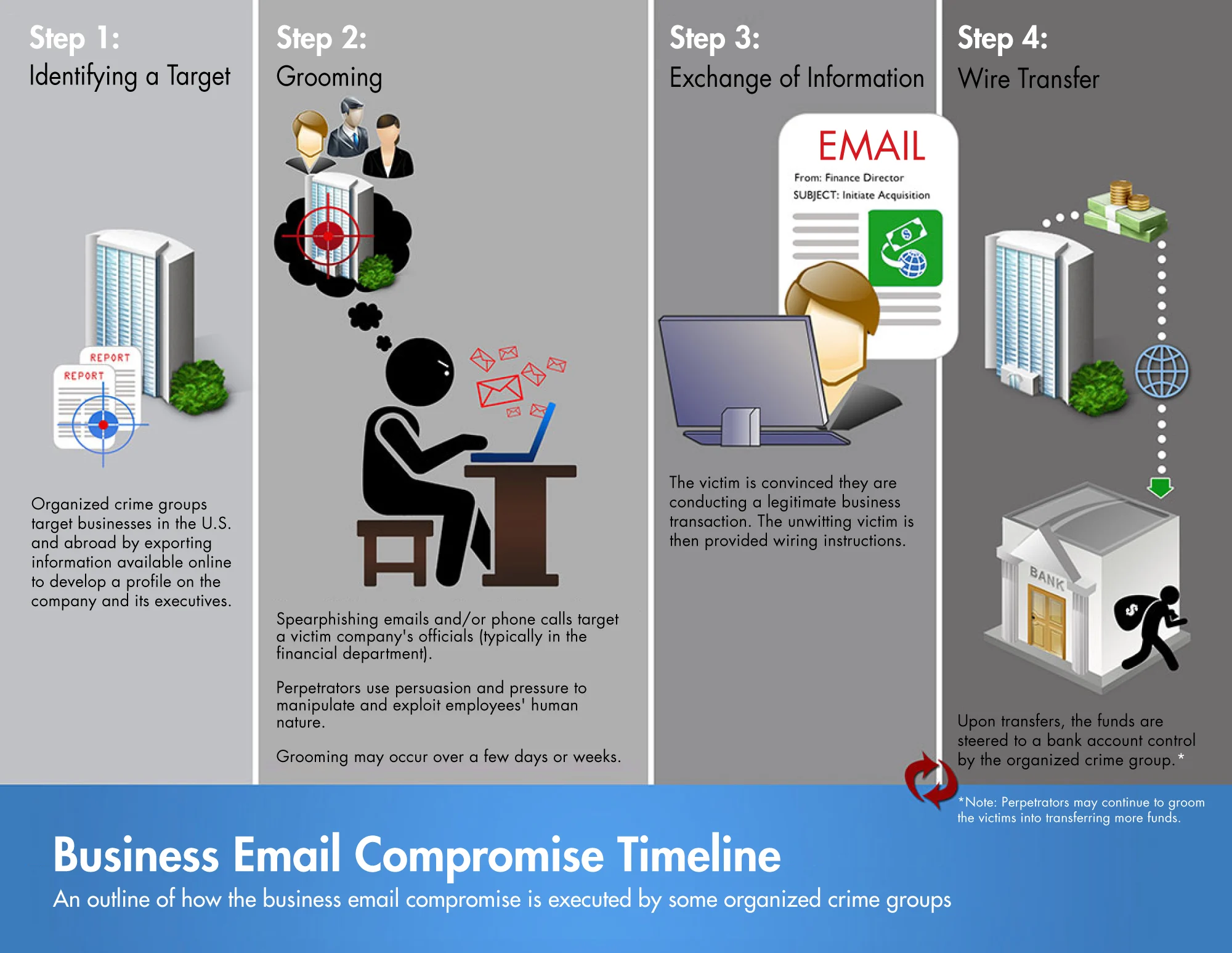
Email remains the primary gateway into most corporate networks. It is also the preferred entry point for cybercriminals because it combines technology weaknesses with human behavior. A single convincing message that appears to come from an executive, vendor, or internal department can bypass traditional security controls and trigger wire transfers, credential theft, or malicious software infections in seconds. For many New Jersey businesses—especially those in professional services, healthcare, construction, logistics, and municipal operations—email compromise has become one of the most financially damaging forms of cybercrime.
Blueclone’s new guide was developed to address the most common breakdowns seen in real incidents: outdated authentication policies, poor visibility into mailbox activity, lack of employee training, and the absence of formal response procedures when suspicious messages are detected. Rather than offering high-level theory, the resource walks organizations through how attackers actually gain access to mailboxes, how they establish persistence, and how internal workflows are often manipulated to move money or sensitive data without triggering alarms.
A central focus of the guide is protecting organizations against executive impersonation and vendor fraud—two of the fastest-growing attack patterns affecting New Jersey companies. In many recent cases, attackers quietly monitor internal conversations for days or weeks after compromising an employee account. Once a payment discussion or contract exchange appears, they insert themselves into the conversation with subtle changes to bank information, payment instructions, or document links. Because the email thread looks legitimate, victims often do not realize a crime has occurred until funds are gone.
The Blueclone guide outlines concrete steps for preventing these attacks, including stronger domain protection, consistent use of multi-factor authentication for all users, advanced phishing detection, and tighter controls over inbox forwarding rules and third-party application access. It also emphasizes the importance of monitoring for anomalous login activity and unusual mailbox behavior—signals that frequently indicate an attacker is already inside the system.
Beyond technical safeguards, the guide stresses that employee awareness is just as critical as software. Modern phishing campaigns increasingly use language, formatting, and tone that closely match legitimate corporate communications. The resource recommends structured, role-specific training for finance teams, executive assistants, IT staff, and operations leaders, ensuring employees who regularly handle sensitive requests can recognize red flags such as urgent payment demands, unexpected document links, and changes to established vendor processes.
For organizations navigating a rapidly changing digital landscape, the guide also serves as a broader reference for evolving cybersecurity and workplace tools. Readers can explore more coverage on enterprise platforms and emerging security solutions through Sunset Daily’s ongoing technology reporting, which tracks how regional businesses are adapting to new digital risks.
Another major component of the Blueclone resource addresses incident response readiness—an area many organizations underestimate. Even companies with modern email filtering and endpoint protection can still experience account compromise. The guide provides a practical response framework for IT and leadership teams, outlining how to immediately isolate affected accounts, preserve evidence, notify internal stakeholders, reset credentials, and validate recent financial transactions. Rapid response, the guide notes, is often the difference between containing an incident and suffering a multi-day operational disruption.
The publication also highlights the importance of aligning email security with broader business continuity planning. Email systems frequently serve as the backbone for scheduling, approvals, document sharing, and customer communication. When access is disrupted during a security incident, organizations can quickly experience cascading delays that affect billing, service delivery, and regulatory obligations. By integrating email protection into business continuity and disaster recovery planning, organizations can reduce operational downtime while maintaining compliance and customer trust.
For New Jersey’s growing ecosystem of professional services firms, healthcare providers, nonprofits, and municipal agencies—many of which operate with lean IT teams—the guide offers a structured, accessible path to strengthening defenses without introducing unnecessary complexity. It outlines how to prioritize protections based on organizational size, risk profile, and regulatory requirements, allowing leaders to make informed decisions about where to invest time and resources.
As digital collaboration continues to accelerate and attackers become more patient and more targeted, email security has shifted from a basic IT responsibility to a core business risk management function. Blueclone Networks’ new Email Security Best Practices Guide reflects that reality, giving organizations across New Jersey a timely, actionable resource to help close security gaps, reduce exposure to financial fraud, and build more resilient communication systems in an era where a single email can determine the outcome of an entire incident.





